TL;DR
- A Chrome extension called Crypto Copilot lets users trade Solana directly from X - but secretly adds an extra transfer sending SOL to the attacker.
- The malware "injects an extra transfer into every Solana swap, siphoning a minimum of 0.0013 SOL or 0.05% of the trade," says cybersecurity firm Socket.
- The extension has been live since June 2024 and remains available despite a takedown request.
- The case adds to a growing list of malicious Chrome extensions targeting crypto users globally.
A Google Chrome extension called Crypto Copilot is drawing attention across the Solana ecosystem - but not for reasons the creators would want. On the surface, the extension looks like a convenience tool, allowing users to execute Solana swaps without leaving their X (formerly Twitter) feed. The idea of trading directly from a social media timeline is attractive, especially for fast-moving Solana traders. But behind that polished UX sits a malicious mechanism quietly shaving off a portion of every swap.
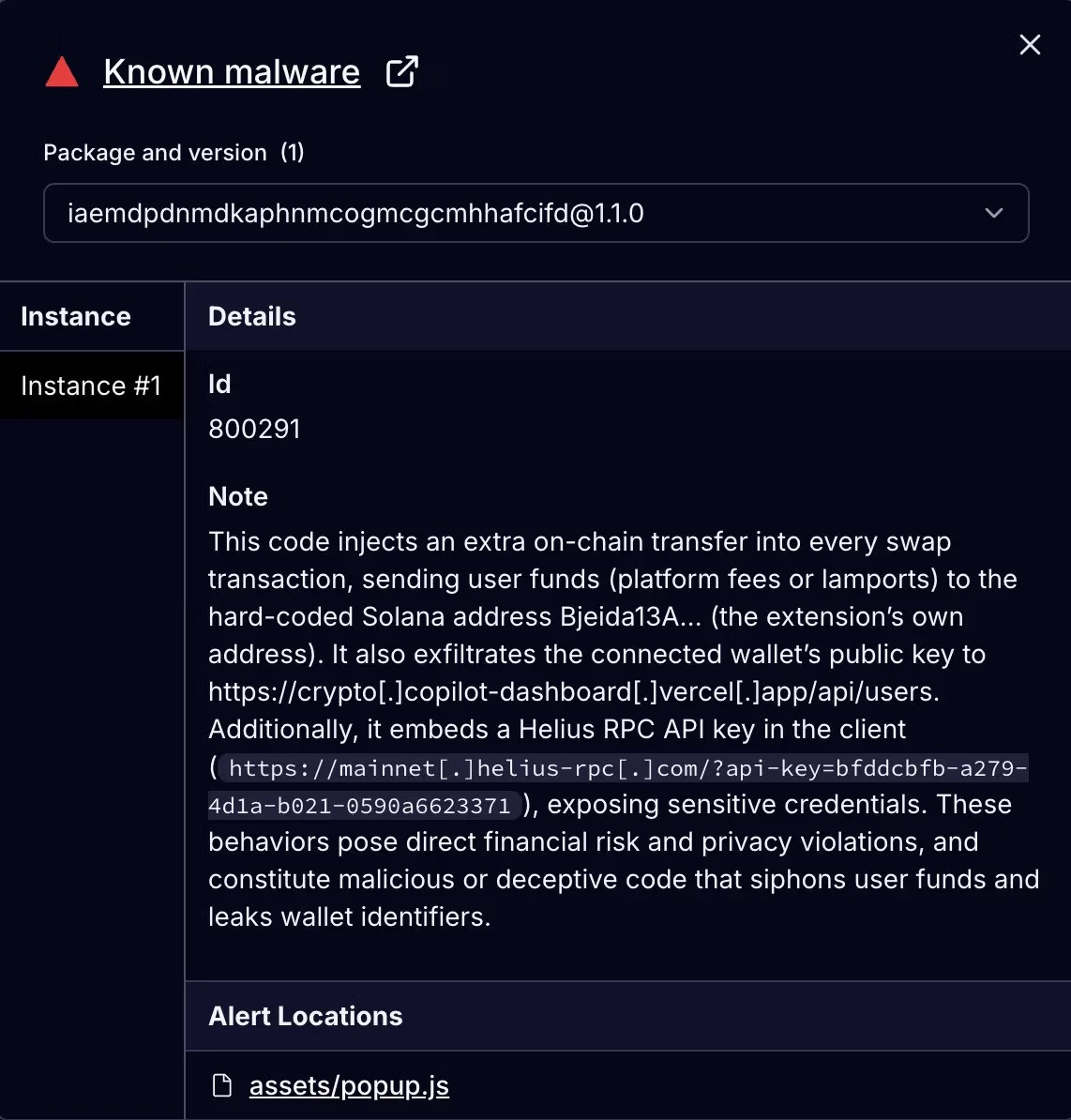
Cybersecurity firm Socket uncovered the hidden behavior, publishing a detailed investigation showing how Crypto Copilot modifies transactions on the back end while showing users only the expected swap interface. According to Socket, the extension "injects an extra transfer into every Solana swap, siphoning a minimum of 0.0013 SOL or 0.05% of the trade," and routes it directly into the attacker's wallet.
The extension doesn't drain wallets outright - a behavior typical of rug-pull wallets and phishing plugins - but instead opts for a more subtle approach: quietly adding a second instruction to each swap, small enough to fly under the radar but significant enough to accumulate if the scam circulates widely.
How the Attack Works Under the Hood
Unlike most aggressive wallet-draining malware, Crypto Copilot takes advantage of Solana's ability to process multiple instructions atomically. The extension uses Raydium, a major Solana-based decentralized exchange, to execute swaps. That part is legitimate. The malicious behavior comes from a second hidden instruction appended after the swap.
Socket explains it clearly:
While the user sees only the swap instruction, the wallet confirmation screen displays a summarized view, meaning the second instruction remains invisible unless the user manually inspects transaction details.
When a user performs a swap, Crypto Copilot builds the expected Raydium swap instruction, then silently adds another step that transfers SOL from the user to the attacker, specifically to this address:
Because Solana transaction instructions are bundled, users end up approving the hidden transfer without realizing it. The entire system is engineered around subtlety. Small fees. Clean UI. Familiar swapping flow. Nothing that raises immediate suspicion. That's what makes operations like this dangerous - they look normal until someone investigates closely.
The Extension Remains Live - And Has Been for Months
One of the more surprising details is that Crypto Copilot is still live in the Chrome Web Store at the time of writing. Socket reported the malicious behavior and submitted a takedown request, but the extension has not yet been removed.
The extension has been available since June 18, 2024, making this a long-lived operation compared to most malicious Chrome extensions, which tend to be discovered and removed quickly. At first glance, it appears almost harmless, with the Chrome Web Store showing around 15 users. But longevity matters more than user count. An extension that stays online for more than a year can be cloned, modified, and redistributed across different channels - Telegram groups, X threads, Discord servers - expanding its reach far beyond the official listing.
And because the extension positions itself as a productivity tool - "allowing you to act on trading opportunities instantly without switching apps" - it's engineered to appeal to impatient, high-activity traders who may not take time to inspect every transaction. That's exactly the population attackers hope to exploit.
Why Chrome Extensions Remain a Major Attack Vector
Crypto Copilot is far from the first malicious extension to target crypto users. Chrome's large user base and flexible extension system have made it a top target for years.
Earlier this month, Socket identified another malicious wallet extension - shockingly, the fourth-most-popular crypto extension in the entire Chrome store - that was actively draining user funds. Jupiter, a major Solana DEX aggregator, also warned in August about a malicious Chrome plugin designed to empty Solana wallets.
And the most dramatic example: in June 2024, a Chinese trader reportedly lost $1 million after installing a Chrome plugin known as Aggr. That plugin stole browser cookies, allowing attackers to take over centralized exchange accounts, including Binance. These incidents point to a pattern: as crypto adoption grows, the easiest vector for attackers isn't smart contracts, blockchain infrastructure or wallet providers - it's the browser environment traders rely on every day.
Chrome doesn't require deep crypto knowledge to exploit. It only requires convincing users to click Install.
Why This Attack Is Different From Typical Wallet Drainers
Most malicious plugins aggressively empty wallets immediately, knowing that security teams respond quickly. Crypto Copilot takes a more restrained approach:
1. It steals in small amounts
Taking 0.05% or a fraction of a SOL each time keeps the activity low enough to avoid triggering alarms.
2. It hides inside normal transaction flows
Users expect swap instructions, so adding a second instruction under the same signature avoids detection.
3. It blends with legitimate Solana infrastructure
By using Raydium as the main swap mechanism, the attack avoids suspicious on-chain patterns that auditors normally flag.
4. It leverages convenience
The idea of trading from X is appealing - something users see as a productivity boost rather than a security risk.
This combination creates an attack pattern that's easy to miss unless someone like Socket examines the code directly.
How Users Can Protect Themselves
The rise of convenience extensions across Solana and Ethereum ecosystems means traders need to rethink how they approach browser-based tools.
A few simple habits dramatically reduce risks:
- Avoid installing extensions from social media posts or small Telegram groups.
- Always check the publisher name and number of reviews.
- When possible, execute swaps directly inside trusted wallets.
- Inspect transaction details when your wallet allows it.
- Prefer official integrations (e.g., Phantom, Solflare, Backpack) instead of third-party overlays.
Crypto Copilot's success - even with only 15 apparent users - shows how easily malicious tools can slip into daily workflows.
Looking Ahead
Crypto Copilot's design shows how attackers are adapting. Wallet drainers are evolving from blunt-force tools into subtle fee siphons. Malware no longer needs to steal everything - it only needs to blend in long enough to steal repeatedly. The Solana ecosystem's rapid growth means more tools, more integrations, and more incentives for attackers to hide inside everyday workflows.
The case also raises a broader industry question: should wallets do more to surface hidden instructions? Should Chrome impose stricter limits on extensions interacting with Web3? Should blockchain explorers highlight suspicious instruction patterns?
Those discussions will likely become more urgent as more cases like this come to light. For now, Crypto Copilot stands as a reminder that convenience always comes with risks - and in Web3, that risk can be measured directly in SOL.











