TL;DR
- Web3 needs stronger privacy as data volume, regulation, and real-world use cases grow.
- The main technologies powering private computation today are GC, ZKPs, MPC, FHE, and TEE, each solving different problems.
- Garbled Circuits (GC) offer the most balanced mix of low latency, trustless design, programmable privacy, and light on-chain storage.
- Zero-Knowledge Proofs (ZKPs) are ideal for verification but limited for fully private computation.
- MPC works well for shared computation but suffers from higher communication overhead.
- FHE provides powerful encryption but remains too slow and computationally heavy for most Web3 apps.
- TEE delivers near-native speed but relies on trusted hardware, creating centralization risks.
- GC's performance and decentralization advantages - especially as implemented by COTI - make it a strong fit for privacy-focused dApps.
The next era of Web3 won't be shaped only by scalability or interoperability. Privacy is quickly becoming the third pillar and perhaps the most important one - as decentralized apps start handling sensitive and high-frequency data. Everything from financial activity and health records to AI-driven decision-making is moving on-chain or working near-chain. At the same time, the amount of personal and behavioral data produced by users has exploded. Cyberattacks, identity theft, data scraping, and large-scale breaches have become a regular occurrence. Governments are tightening data protection laws. Enterprises are looking for ways to adopt decentralized infrastructure without exposing confidential information.
All of this puts pressure on Web3 developers to design applications that stay transparent without revealing everything. And right now, five major privacy technologies are shaping how the next generation of apps will function: Garbled Circuits (GC), Zero-Knowledge Proofs (ZKPs), Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Trusted Execution Environments (TEEs).
Each one answers different needs and each one comes with trade-offs. This article breaks down how they work, where they struggle, and why GC is emerging as a highly practical option for developers who want strong privacy without giving up performance or decentralization.
Why Privacy Is Becoming a Core Requirement for Web3
Privacy used to be treated as an optional feature - something a few projects offered or a niche audience demanded. That has changed quickly. Today's decentralized applications operate in environments where:
- Real identities are tied to wallets.
- AI models push computations on-chain.
- Enterprises evaluate blockchain as a backend for sensitive data.
- Users expect confidentiality similar to Web2 apps.
- Regulators demand strong encryption, auditability, and compliant privacy.
This shift creates a paradox: blockchains are transparent by default, but real-world adoption requires selective confidentiality. The missing piece is trustless private computation, where data can be processed without revealing anything sensitive to validators, the network, or other users. That's where these five technologies come into play - and where their limitations start to become visible when used in live systems.
Why Current Privacy Models Fall Short
Most teams entering the privacy-computing space quickly realize that the existing options come with serious trade-offs. The tools we currently rely on-whether they're cryptographic systems or hardware-based solutions-weren't designed to handle the scale, speed, or flexibility that modern decentralized apps now demand. Developers often face a frustrating mix of performance issues, expensive computation, strict hardware requirements, and models that introduce some form of centralization. Even when a technology promises strong security, it usually sacrifices something essential elsewhere, like latency, device compatibility, or ease of deployment.
On paper, many of these privacy systems look complete, but in practice, they force builders to choose between privacy and usability. Some models are simply too computationally heavy to support real-time applications. Others depend on trusted hardware or closed ecosystems that clash with the core idea of a decentralized environment. And some require sophisticated setups that only highly specialized teams can implement. The result is that most projects struggle to ship private smart contracts that are fast, affordable, and trustless at the same time.
This gap is becoming more visible as Web3 matures. Users expect stronger protections, regulators expect compliance, and teams want privacy tools that don't slow everything down. But the current models rarely deliver all three-speed, security, and decentralization-together. That's why the industry is shifting toward approaches that offer complete confidentiality without forcing developers to compromise on performance or infrastructure. The need for a more balanced solution is clearer than ever.
The Five Major Privacy Technologies
Here's the full landscape at a glance:

Garbled Circuits (GC) : A cryptographic method enabling multiple parties to compute functions together without revealing their inputs - fast, lightweight, and fully trustless.
Zero-Knowledge Proofs (ZKPs): A way to prove that something is true without revealing the underlying data.
Multi-Party Computation (MPC): Allows several parties to jointly compute a result while keeping individual inputs private.
Fully Homomorphic Encryption (FHE): Enables computation on encrypted data without needing to decrypt it first.
Trusted Execution Environments (TEE): Hardware-based isolated environments where code executes privately inside a secure enclave.
With these definitions, we can explore how each behaves when applied to real-world Web3 use cases.
Deep Dive: Garbled Circuits (GC)
Garbled Circuits were introduced in the 1980s as a purely theoretical concept for secure computation. For decades, they remained too heavy and too slow to be used in real systems.
COTI changed that. By optimizing GC to run efficiently on-chain, COTI turned a long-standing theoretical model into a practical tool for private decentralized apps. The result is privacy computation that is:
- Fast - up to 3000x faster than FHE.
- Lightweight - around 250x less computationally heavy than FHE.
- Fully trustless - no hardware assumptions or privileged nodes.
- Programmable - supports full private logic, not just proofs.
- Universal - compatible with all chains, all devices, and any computation.
How It Works (Simple Explanation)
Imagine two parties want to compute an outcome without showing their inputs. GC transforms the computation into a scrambled circuit that only reveals the final result. No one sees anything except what the function outputs.
What makes GC valuable today is that:
- It's fast enough for live applications like auctions, lending, governance, gaming, and AI inference.
- It's flexible enough to replace traditional private smart contract execution.
- It avoids trusted hardware, which aligns with blockchain values.
For enterprises, it provides privacy without forcing them to rely on external hardware or specialized infrastructure - a major advantage for compliance and risk management.
Deep Dive: Zero-Knowledge Proofs (ZKPs)
ZKPs have become one of the most recognized technologies in crypto thanks to their role in rollups and private transactions.
Where They Excel
They are ideal for proving something without revealing the underlying information. For example:
- Proving you own a credential without showing it.
- Proving transaction validity without exposing details.
- Scaling blockchains by verifying large computations succinctly.
Where They Struggle
ZKPs are limited when it comes to full private computation:
- They don't support programmable privacy - they prove facts but don't hide logic during runtime.
- They face big latency trade-offs when computations get complex.
- They often require custom circuits and specialized developer knowledge.
- Device compatibility is limited because proof generation can be heavy.
ZKPs are essential - but they're not a full privacy stack on their own.
Deep Dive: Multi-Party Computation (MPC)
MPC allows several participants to compute a result without revealing individual inputs. It's useful in scenarios like collaborative decision-making or shared secrets.
Strengths
- Strong privacy without needing trusted hardware.
- Resilient because no single party controls the system.
- Useful for threshold signatures and custody setups.
Limitations
- Requires ongoing communication between participants.
- Latency increases with network delays.
- Harder to scale to thousands or millions of users.
- Heavier on-chain footprint due to data exchange.
- Not ideal for real-time decentralized apps.
MPC is powerful but tends to be slow and infrastructure-heavy.
Deep Dive: Fully Homomorphic Encryption (FHE)
FHE is often described as a "holy grail" of privacy because it allows computation directly on encrypted data.
Where It Shines
- Maximum confidentiality - everything stays encrypted at all times.
- Particularly strong for highly sensitive offline processing.
Where It Falls Short
Despite progress from teams like Zama, Intel, and others, FHE remains:
- Extremely slow compared to GC or TEEs.
- Very resource-intensive.
- Hard to run on consumer devices.
- Limited for real-time use cases in DeFi or gaming.
Most teams see FHE as a future technology, not a present one.
Deep Dive: Trusted Execution Environments (TEE)
TEEs create secure enclaves inside hardware where code runs privately. Intel SGX, AMD SEV, and ARM TrustZone are the main providers.
Where They Excel
- Very fast - near-native execution.
- Easy to integrate.
- Good for private AI inference or enterprise use.
Where They Struggle
The main issue is centralization:
- You must trust the chip manufacturer.
- Hardware vulnerabilities can break the entire model.
- A single point of failure is built into the system.
TEEs bring speed, but at the cost of decentralization - which makes them imperfect for many Web3 use cases.
Which Technology Fits Which Use Case?

Every privacy technology in Web3 solves a different problem. The mistake most teams make is assuming there's a single "perfect" model that works everywhere. In reality, each approach fits a specific type of application, and understanding these boundaries is what separates workable designs from over-engineered prototypes.
Zero-knowledge proofs are ideal when the only thing that matters is proving a statement-nothing more. They shine in situations where a user needs to verify an action or fact without exposing the underlying data. Think of compliance checks, proof-of-funds, or identity confirmations. They're not built for full private computation, but when the requirement is narrowly focused verification, ZK does the job cleanly.
MPC fits a different class of problems. It works best when multiple parties want to collaborate without trusting each other, usually around shared secrets or joint decision-making. Wallet-level key management and institutional custody are strong examples. MPC keeps everything distributed but struggles the moment the application needs fast, complex computation or real-time interaction.
FHE looks perfect on paper-encrypted inputs, encrypted processing, encrypted outputs. It's the strongest form of confidentiality. But its computational weight means it fits only the most specialized cases, usually environments where privacy matters more than performance. Medical data, long-term analytics, and sensitive enterprise workflows fall into this category, where latency isn't a deal-breaker.
TEEs sit on the opposite end of the spectrum. They're fast and convenient, which is why companies use them for secure enclaves and low-latency workloads. But they depend on trusted hardware, and that introduces centralization and supply-chain risks that many decentralized apps try to avoid. TEEs work best where speed is non-negotiable and the trust model is acceptable-for example, regulated environments or internal enterprise systems.
Garbled Circuits fill the gap that none of the others cover. They support full confidential computation, handle multi-party logic, keep latency low, and avoid reliance on trusted hardware. That makes them suitable for real-time apps where both privacy and decentralization matter-private auctions, confidential DeFi logic, on-chain AI inference, or any workflow that needs programmable confidentiality without slowing to a crawl.
Each technology holds its place in the ecosystem. The key is matching the cryptographic tool to the real needs of the application instead of forcing a system into a model it wasn't built for. GC stands out because it offers a middle ground where speed, privacy, and decentralization can coexist, something most other models can't deliver at the same time.
Why GC Is Emerging as the Most Balanced Solution
When you combine performance, decentralization, and broad compatibility, GC covers more ground than the rest. It avoids the hardware trust issues of TEEs, the computational weight of FHE, the communication burden of MPC, and the programmability limitations of ZKPs.
COTI's implementation pushes it further by making GC accessible to EVM developers, keeping it chain-agnostic, and enabling high-frequency applications like auctions, governance, lending, and AI-driven logic. As Web3 shifts toward real-world adoption, GC brings a practical path for confidential computation that doesn't force developers to sacrifice speed or decentralization.
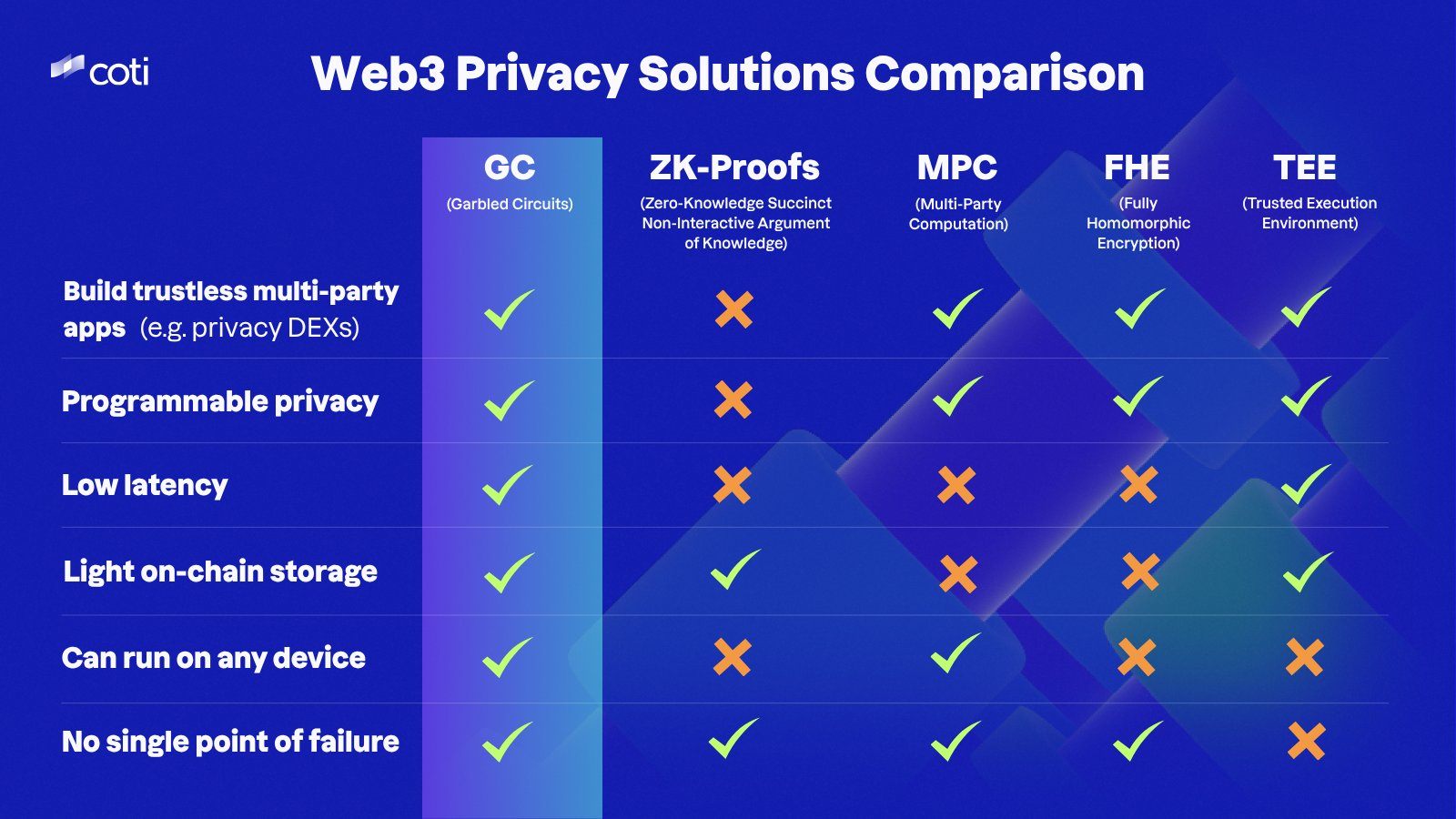
COTI's comparison highlights why GC stands out: it balances privacy, speed, scalability, and decentralization without forcing developers to compromise.
Final Thoughts
Web3 privacy is entering a new phase - one where developers need tools that work today, not just ideas that might become feasible years from now. Each technology contributes something meaningful, but the market is clearly shifting toward approaches that blend performance, confidentiality, and decentralization.
Garbled Circuits are becoming a strong contender for that role. As more builders explore trustless privacy for dApps, GC's flexible and lightweight model fits the direction the ecosystem is moving. And with players like COTI pushing GC toward real production environments, developers finally have a privacy framework that feels both powerful and practical.
This is only the beginning. As applications become more complex, the importance of private computation will grow. And the technologies that balance usability with real security will define the next generation of decentralized apps.










