TL;DR
- Pepe memecoin's official website has been compromised and is redirecting visitors to a malicious link.
- Blockaid identified the attack as a front-end exploit containing Inferno Drainer code.
- Users are urged to avoid the website completely until a full fix is confirmed.
- PEPE's price remained mostly stable in the short term despite the incident.
- The hack adds to growing concerns about rising front-end attacks across major crypto websites and memecoins.
The official website for Pepe has been hit by a coordinated front-end attack, marking another high-visibility incident targeting one of crypto's largest memecoin ecosystems. Cybersecurity firm Blockaid was first to raise the alarm, reporting that the site had been compromised and was now redirecting users to a malicious link. The warning was direct:
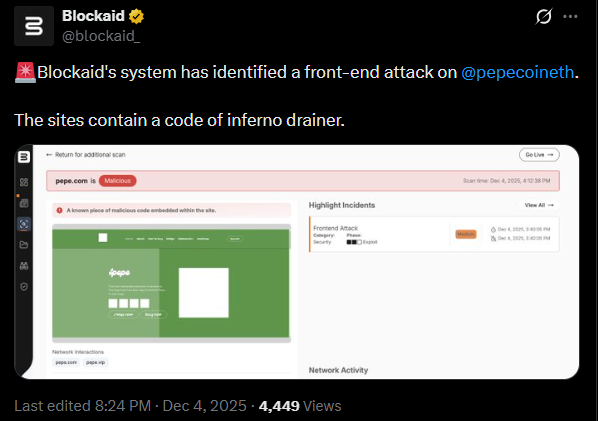
The discovery suggests attackers managed to inject malicious JavaScript into the website's interface layer - a tactic that has rapidly grown more common in 2024-2025 as hackers shift their focus from smart contract exploits to user-facing weaknesses.
Users attempting to access the Pepe website are being redirected toward malware designed to steal assets, drain wallets, or trick users into authorizing harmful transactions. At the time of writing, the site remains unsafe to visit, and users are strongly advised to stay away until the development team issues a formal all-clear.
What Is Inferno Drainer and Why It's Dangerous
Inferno Drainer is widely considered one of the most aggressive and effective drainer kits in circulation. It's not just malware-it's an entire operational toolkit, usually sold to threat actors in underground markets.
It includes:
- Phishing site templates,
- Wallet-draining scripts,
- Social engineering add-ons,
- Automated transaction-signing traps.
Once users connect a wallet or approve a malicious signature, Inferno Drainer can empty assets within seconds. This is why front-end attacks are so concerning: the user believes they are interacting with the official website, not a counterfeit one.
Because the exploit was injected into the authentic domain rather than a fake look-alike site, even experienced users are at risk.
Market Reaction: PEPE Price Holds Despite The Incident
Despite the severity of the exploit, PEPE's price did not immediately reflect the panic one might expect. The memecoin is up about 4.20% over the past 24 hours, according to CoinMarketCap. However, broader sentiment remains shaky, as the token is still down more than 16.33% over the past month.
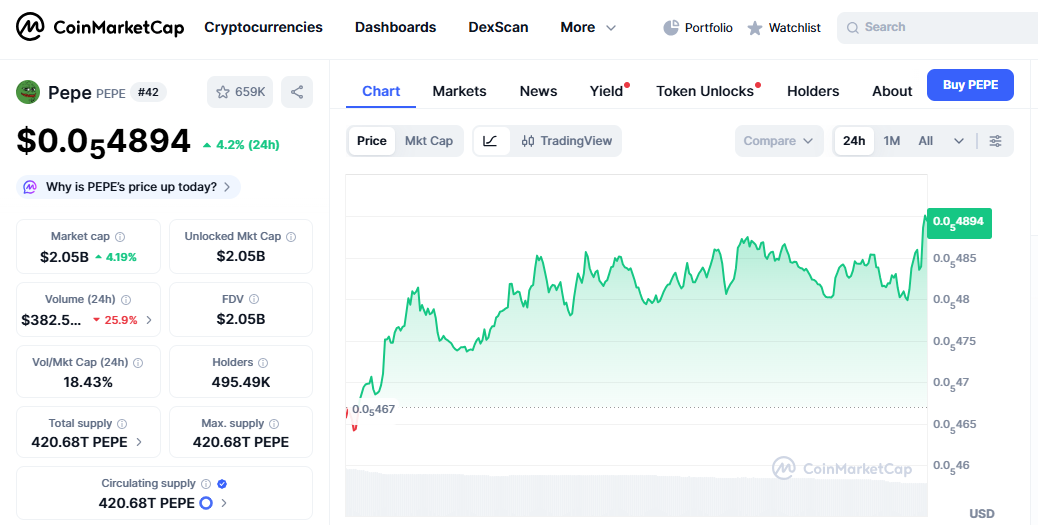
This divergence - rising short-term price despite long-term decline - suggests a divided market: short-term traders are unfazed, but longer-term holders remain cautious. Similar incidents across other memecoins and NFT ecosystems in recent years have shown that price reactions typically lag behind public disclosure, depending largely on how quickly teams respond and how much damage users report.
Why Front-End Attacks Are Becoming So Common
The crypto industry has spent years tightening smart contract code, auditing deployers, and reinforcing protocols. In response, attackers have begun focusing on front-end infrastructure, where they face fewer protections and can strike a larger audience with a single breach.
Front-end compromises usually occur through:
- Leaked contributor credentials,
- Outdated CMS frameworks,
- Third-party service exploits,
- DNS hijacking or routing manipulation.
Because users rely heavily on trust signals like domain names and official branding, front-end attacks convert that trust into vulnerability. The attacker doesn't have to break a smart contract - they only need to intercept a few lines of code loaded by the website.
Memecoins have become especially attractive targets because:
- Their communities are large and active
- Traffic spikes frequently
- New users often visit official sites to check updates.
This Pepe attack fits the broader pattern.
Community Response and Immediate Safety Measures
For now, the advice is simple: Do not visit the Pepe website until the team confirms the breach has been resolved. Even loading a website with malicious scripts can place users at risk, particularly if the script attempts to spoof wallet pop-ups or quietly connect to browser extensions.
Recommended precautions:
- Avoid interacting with any dApp prompts originating from the Pepe domain.
- Do not approve transactions related to Pepe until the team issues a verified statement.
- Revoke approvals if you suspect exposure to a malicious session.
- Use independent security checks before signing anything.
Cybersecurity firms like Blockaid and Blowfish have consistently urged users to assume zero trust when browsing compromised sites - even briefly.
Final Thoughts
The compromise of Pepe's website is a reminder of how fragile front-end security can be, even for major projects. While the token's price hasn't collapsed, the reputational risk is real, and the situation underscores the ongoing need for caution whenever interacting with crypto websites.
Until the team confirms full remediation, users should treat the site as unsafe and avoid interacting with it entirely. Stay safe, double-check everything, and avoid connecting your wallet to any site flagged by credible security firms.











